Detecting Cyber Threats with MITRE ATT&CK App for Splunk — Part 1
The purpose of this blog post is to share our experience and knowledge in our attempts to detect cyber threats with Splunk®. Since we have a knowledge base of adversary behavior (MITRE ATT&CK) and an analytics-driven platform (Splunk) that helps us identify, investigate, respond to threats; it would be best to combine these features for a better detection mechanism.
About MITRE ATT&CK® Framework
Within cyber security industry, MITRE ATT&CK® Framework has gained a lot of popularity and adoption by various vendors. The definition from MITRE is as following:
“MITRE ATT&CK® is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations.”
The framework provides great guidance on how to approach cyber security related issues based on 4 use-cases:
- Threat intelligence
- Detection and analytics
- Adversary emulation and red teaming
- Assessment and engineering
In this blog the focus is on utilizing Splunk to address Detection and Assessment use-cases with MITRE ATT&CK framework.
About Splunk ES & ESCU
Splunk is a flexible platform enabling users to monitor and analyze machine data from any source.
Splunk Enterprise Security is the security information and event management (SIEM) solution that is built on top of Splunk Enterprise.
Splunk ES Content Update delivers pre-packaged security content with “Analytic Stories” (analysis guides). These include ready to implement correlation rules as well as guidance on security context and risks associated with attack techniques/tactics.
For the purposes of this blog, you should be somewhat familiar with Splunk notable event and incident review dashboard.
Notable event: An event generated by a correlation search as an alert. A notable event includes custom metadata fields to assist in the investigation of the alert conditions and to track event remediation.
Incident Review dashboard surfaces all notable events, and categorizes them by potential severity so you can quickly triage, assign, and track issues.
Need for Analysis: MITRE ATT&CK App for Splunk
One of our customers asked us if it’s possible to visualize real-time attack/threat information as MITRE ATT&CK matrix within Splunk. The framework is a great reference point and it is very helpful to utilize ATT&CK Navigator for visualization; however, not all organizations have the resources to investigate and update this information continuously. So, we tried to keep it simple for the end-user and focus on detection and assessment use-cases and integrating this with Splunk ES capabilities:
Detect: Display real-time notable events triggered within MITRE ATT&CK matrix Assess: Display how current available/enabled correlation rules stack up to techniques/tactics in MITRE ATT&CK Result: MITRE ATT&CK App for Splunk
This application provides compliance and triage dashboards for MITRE ATT&CK Framework that are fully integrated with Splunk Enterprise Security and Splunk ES Content Update with drill-down capabilities.
Note: Detailed documentation for the app can be found here.
I will share some of the views/screenshots from this application and try to explain how these views address the above use-cases. In order to get started, we have to have some baseline and rules enabled. The application starts with the following view for assessment purposes:
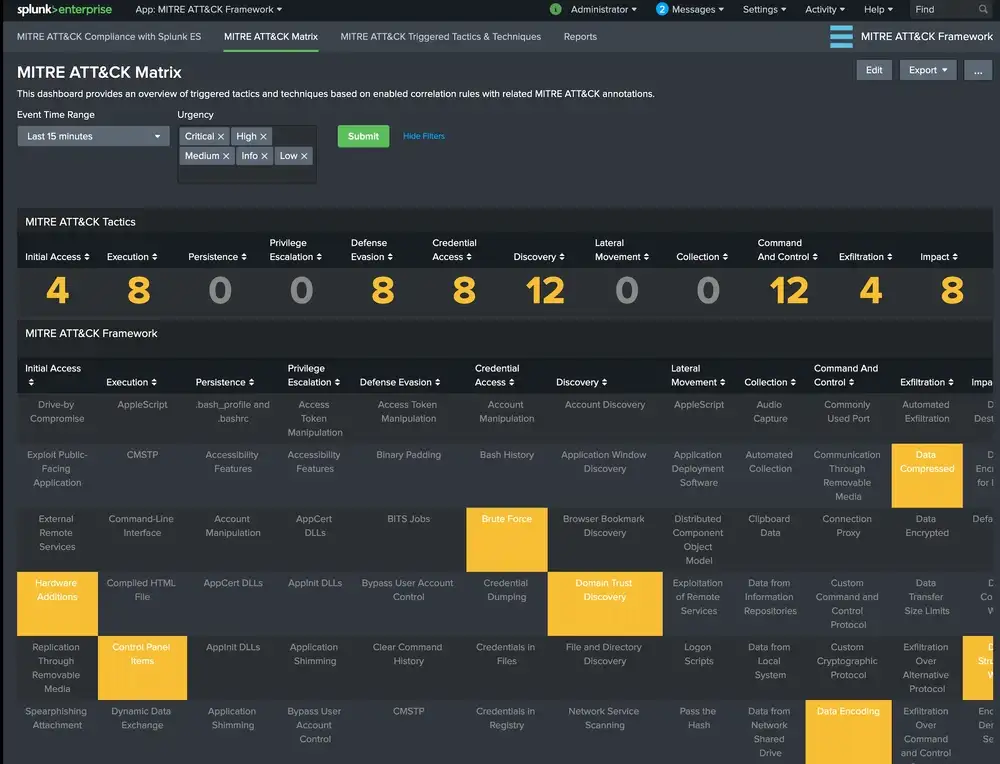
Things to consider about this view:
- Each cell containing a technique is colored based on the percentage of enabled correlation searches.
- If there is not any related correlation searches, the cell is left uncolored.
- If there are available correlation searches within Enterprise Security (and ESCU), then cells are colored based on percentage of enabled/active ones. Currently the ranges are set as follows:
- none: 0–30% (uncolored)
- low: 30–50% enabled
- medium: 50–70% enabled
- high: 70%+ enabled
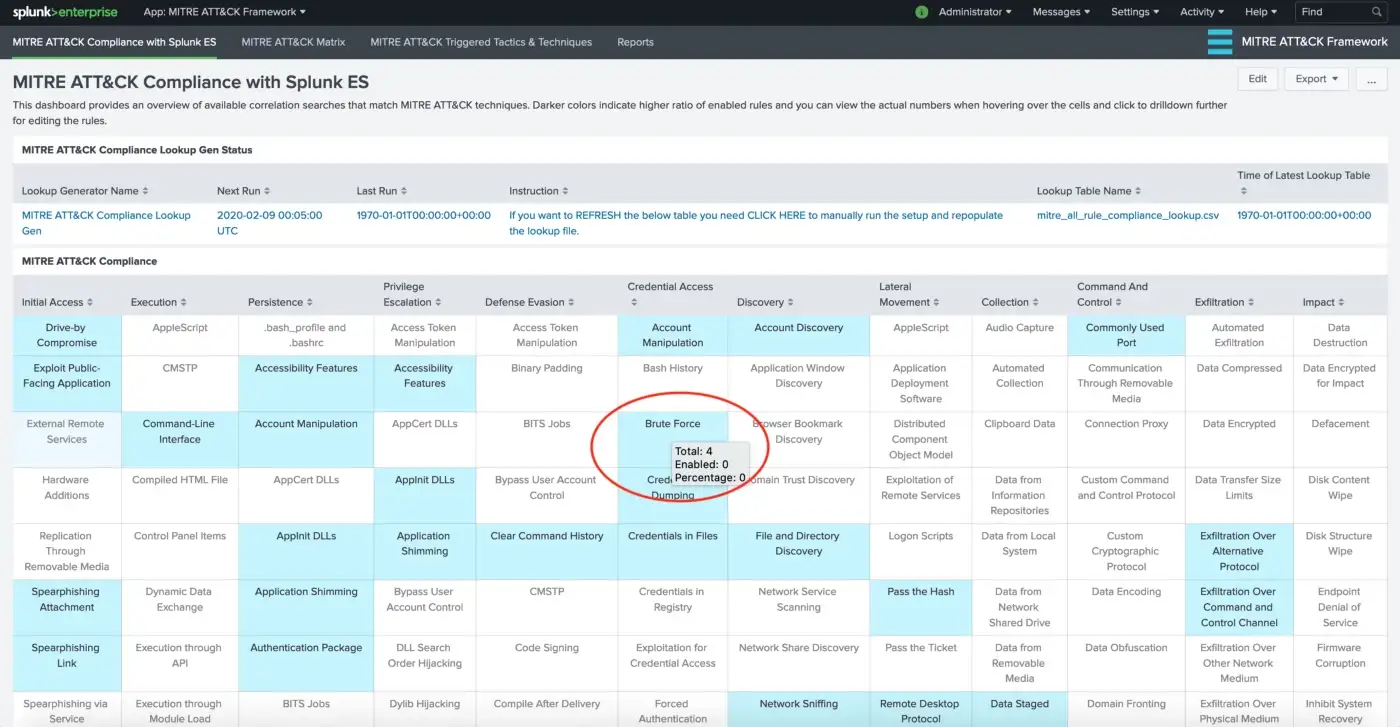
- You can click on a specific technique in order to view the associated correlation rules within ES App. This takes you to MITRE ATT&CK Rule Finder view, which enables users to search for existing correlation rules based on technique names.
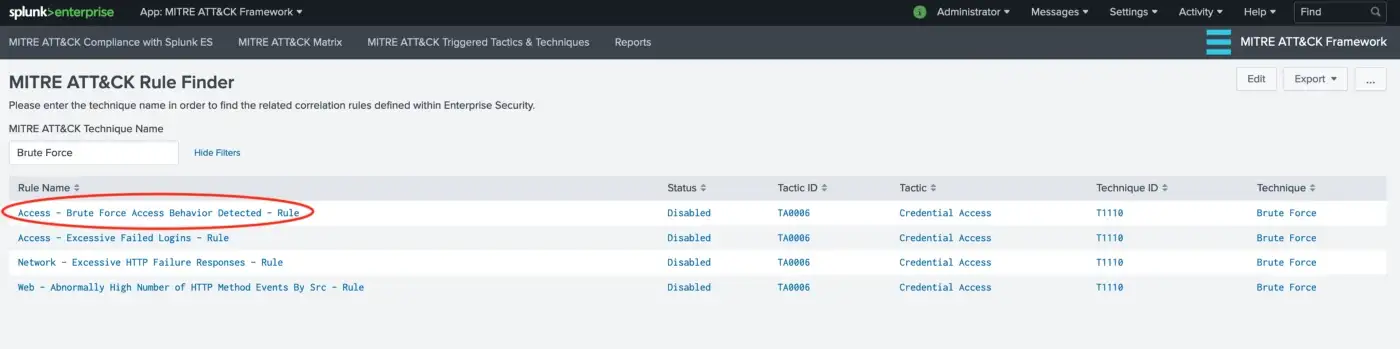
You can click on the desired rule for further configuration (enable/edit rules, etc.). This will take you to Enterprise Security configuration for editing.
Once the rules are configured and enabled you can view the MITRE ATT&CK Matrix view for the current status of related correlation rules within a given time frame. It provides and overview of triggered techniques within MITRE ATT&CK Matrix colored according to the “Urgency” level of Notable Events.
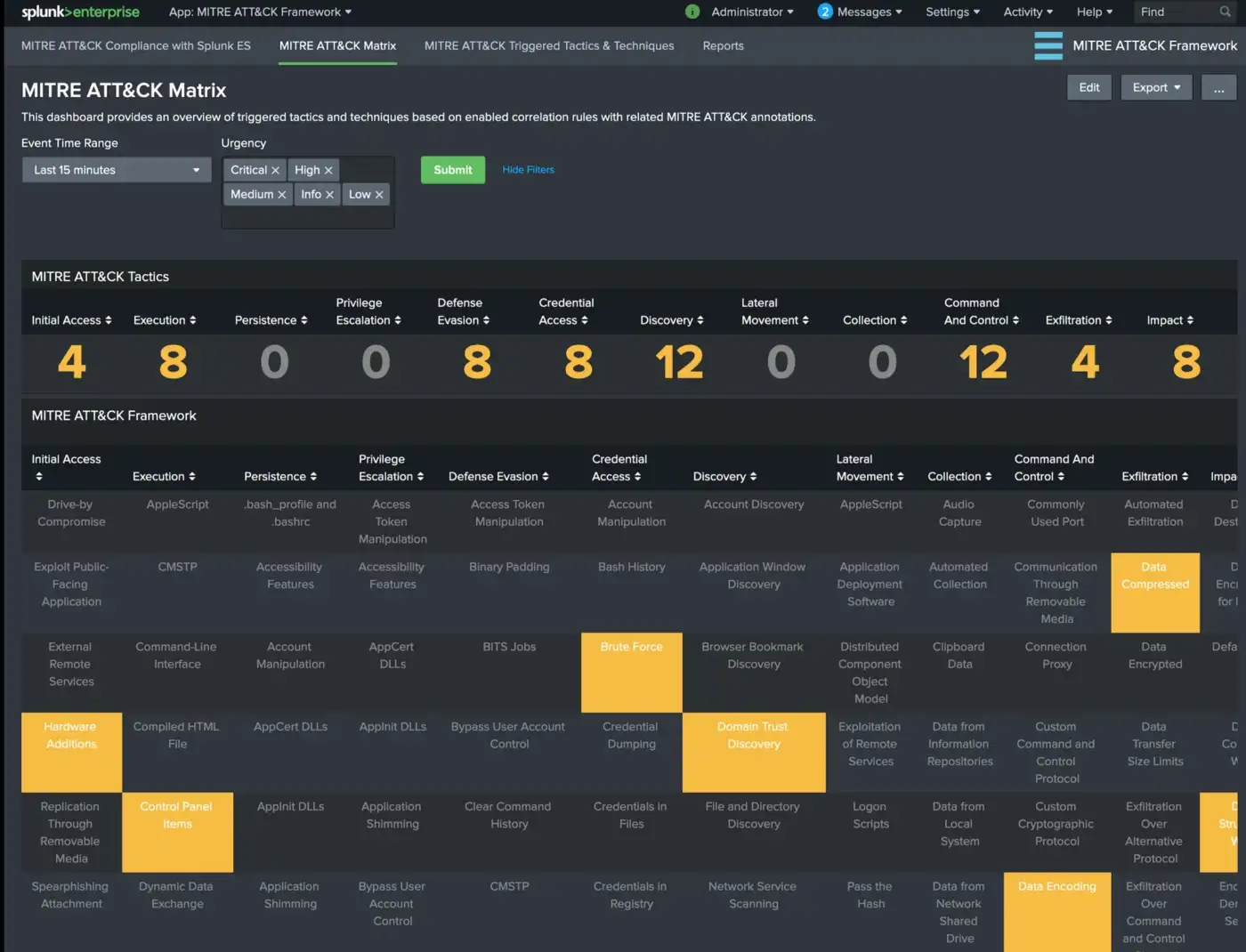
You can click on the triggered technique which provides the drill-down functionality and opens up Enterprise Security App Incident Review view for further analysis/investigation.
There’s also an additional view within this app for further analysis of detection use-cases based on triggered tactics and techniques.
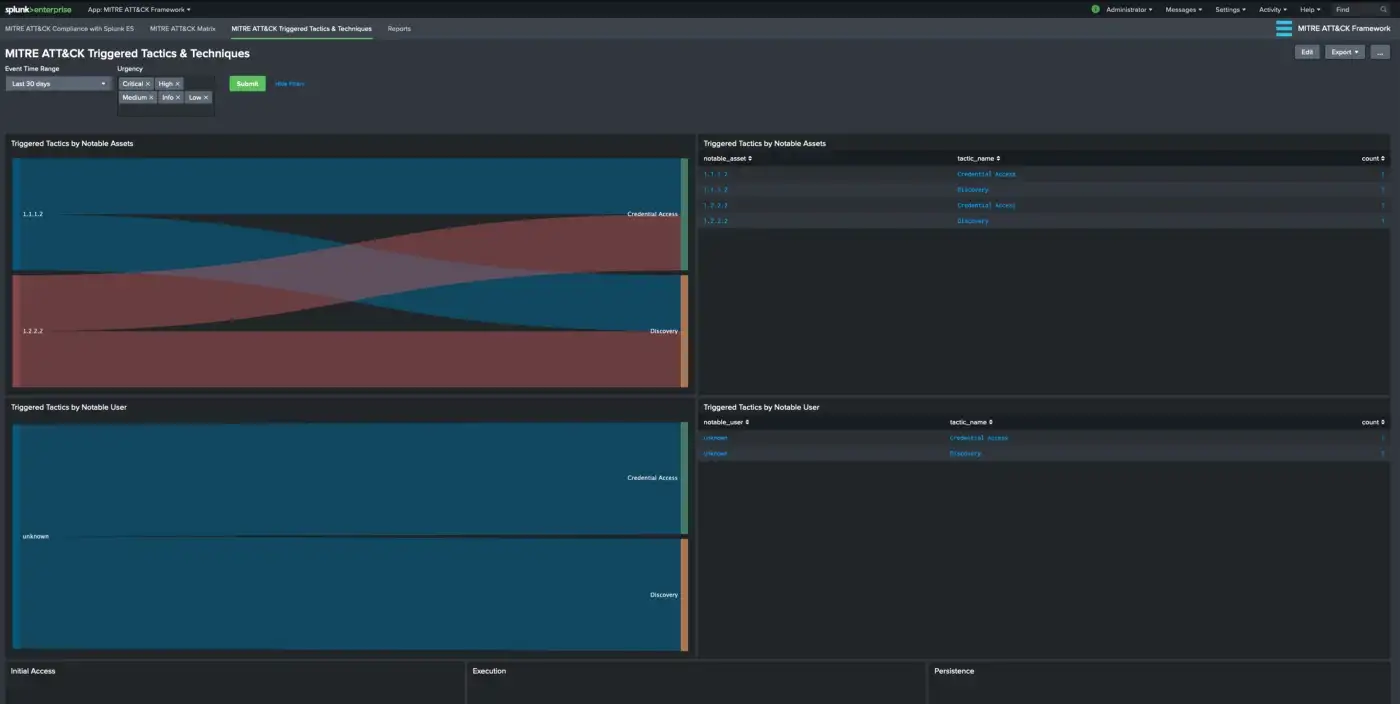
This visualization provides an overview of triggered rules (notable events) based on MITRE ATT&CK Tactics and Notable assets/identities. The number of triggered Notable Events according to MITRE ATT&CK techniques are aggregated by Notable Assets where notable_asset is populated by src, dest or user fields from related Data Models.
This is an effort to provide a better visibility for a notable asset/identity journey through MITRE ATT&CK Framework. Knowing which techniques are triggered is a great way to get started but knowing the journey of an identity/asset through tactics may become more beneficial. For example, within a certain time frame we can see an asset (e.g. IP address within our network) as a destination for a technique under “Initial Access” and view the same asset as a source for a technique under “Command and Control”.
How to get started?
Installation of MITRE ATT&CK App for Splunk is pretty straight forward. You can download it from Splunkbase and install on your Splunk Search Head where Enterprise Security application is installed. Step-by-step instructions can be found here.
The visualizations depend on lookup tables and those lookup tables are scheduled to run at midnight every day by default. This schedule is configurable according to your needs of course (i.e. Lookup generator search). Upon the initial installation, you may need to visit the setup dashboard to trigger the searches that populate the lookup tables to get things started right away.
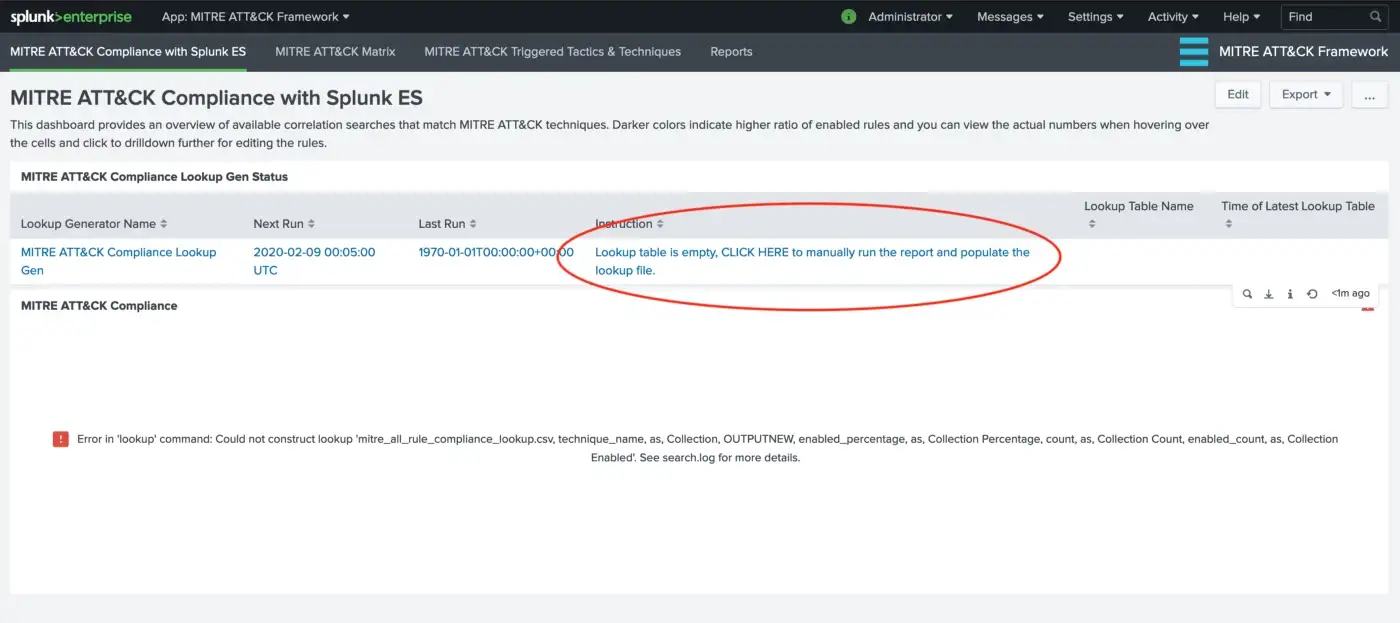
Click on the table row.
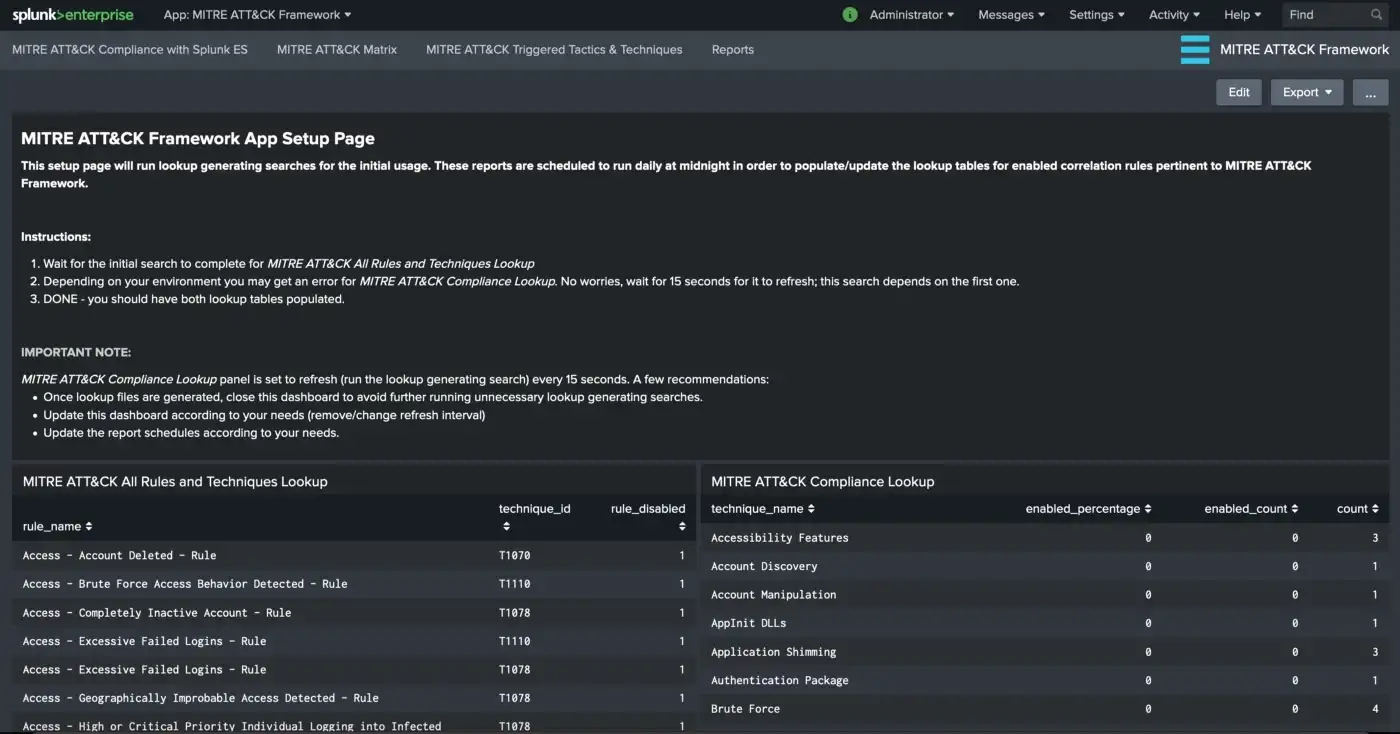
Once on the setup page, just wait for the searches to complete and you’re done!
What’s Next?
In this part of the series I wanted to go over the basics of MITRE ATT&CK framework and how we can utilize Splunk (and specifically MITRE ATT&CK App for Splunk) to get things started on our way to finding/detecting cyber threats. On the next part of the series we will review how to add custom correlation rules to Splunk that match with MITRE ATT&CK techniques.
Part 2 of the series can be found here.
References:
- MITRE ATT&CK
- Getting Started with ATT&CK eBook
- Finding Cyber Threats with ATT&CK-Based Analytics
- ATT&CK 101
- ATT&CK Navigator
- ATT&CK Navigator (github)
- Splunk Enterprise
- Splunk Enterprise Security
- Splunk ES Content Update
- MITRE ATT&CK App for Splunk
- Documentation for MITRE ATT&CK App for Splunk
- Splunk notable event
- Splunk Incident Review


