Splunk
Upgrading Splunk ES from 7.x to 8.1.1 - Our Journey and Lessons Learned
Upgrading from Splunk ES 7.x to 8.1.1 isn’t just a version change — it’s a structured transition that, with the right preparation and automation, can be smooth, controlled, and operationally safe.

Bridging LLMs and Operational Data with MCP Using Splunk
This article explores the core concepts of Model Context Protocol (MCP) and MCP Servers, and demonstrates how they can be applied in a real-world Splunk use case using Claude.
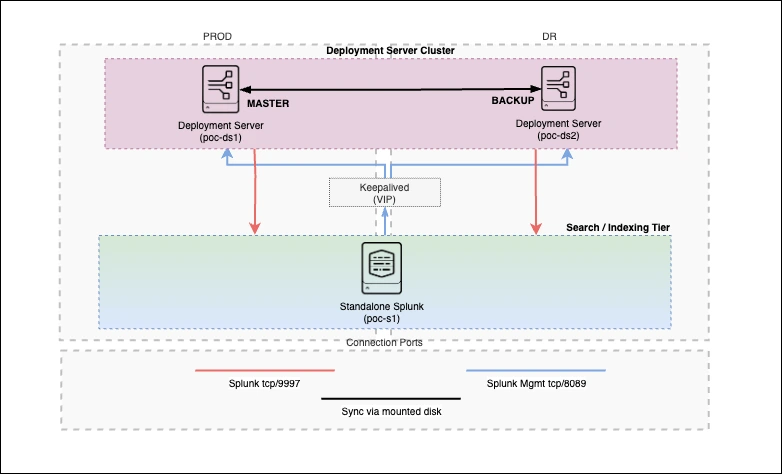
Building a Highly Available Splunk Deployment Server Cluster (POC)
A hands-on, honest POC story: why we needed Deployment Server redundancy in Splunk, what we tried, what worked, and what we learned along the way.
📘 Part 2: Behavioral ML for Windows Authentication — From Data to Dashboards
Running the ML Sidecar end-to-end: ingesting data, executing the pipeline, and exploring dashboards.

📘 Part 1: Behavioral ML for Windows Authentication: Concepts & Engine
ML Sidecar is an experimental Python engine that models “normal” authentication behavior, scores deviations from multiple perspectives, and turns them into flexible, explainable outlier signals for Splunk.

PART 2 — Distributed Splunk in Docker: Forwarder Architecture & Data Ingestion Pipeline
In this two-part article series, this part focuses on log onboarding using Universal and Heavy Forwarders within a containerized distributed Splunk environment.

PART 1 — Distributed Splunk in Docker: Building a Complete Clustered Architecture
This two-part article series demonstrates how to build a fully containerized distributed Splunk environment in Docker. Part 1 focuses on the clustered architecture and deployment, while Part 2 covers log ingestion using forwarders.

Restore Splunk Frozen Buckets Easily: Local, S3, or Custom S3-Compatible Storage
Easily restore frozen Splunk data from local storage, AWS S3, or S3-compatible endpoints using a flexible Python-based utility.

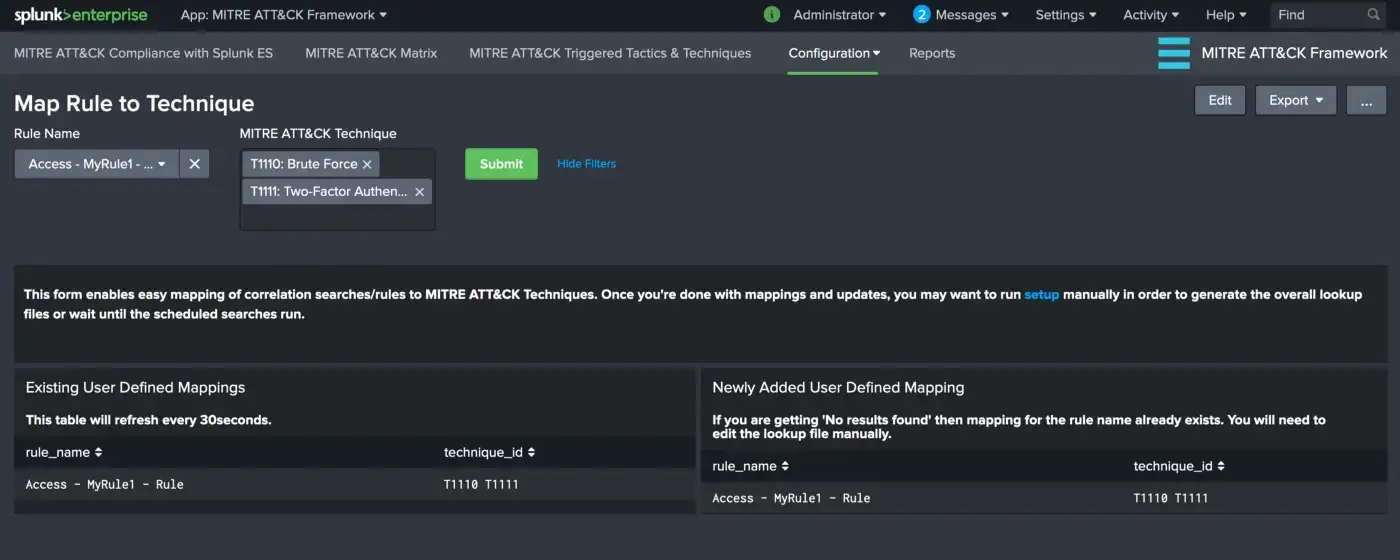
MITRE ATT&CK App for Splunk 3.14.0 — Release Highlights
This guide highlights the new features in MITRE ATT&CK App for Splunk 3.14.0, including a redesigned dashboard layout, a threat actor lookup, and improved visualizations to streamline ATT&CK-based threat detection and analysis.

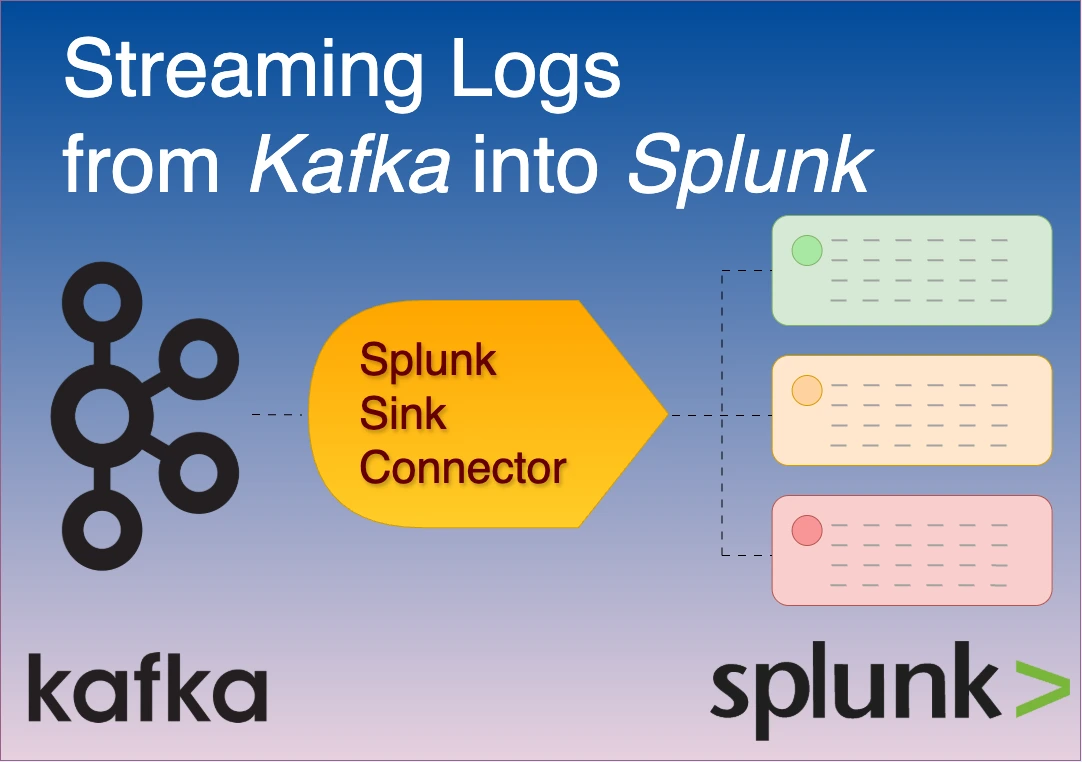
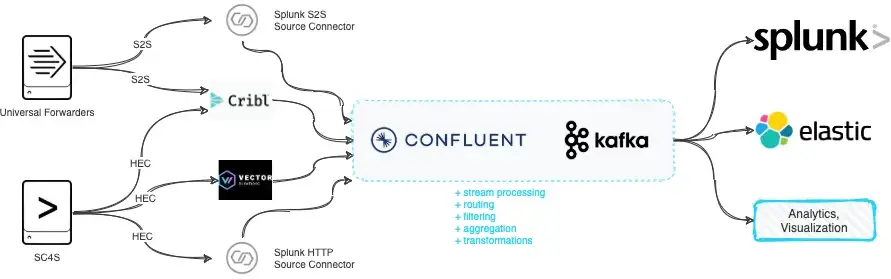
Streaming Logs from Kafka to Splunk using the Splunk Sink Connector
In this blog, I show how to stream Fortinet logs from Kafka into Splunk using the Splunk Sink Connector — no SC4S, no intermediate scripts, just clean, timestamped data ready for dashboards and detection.
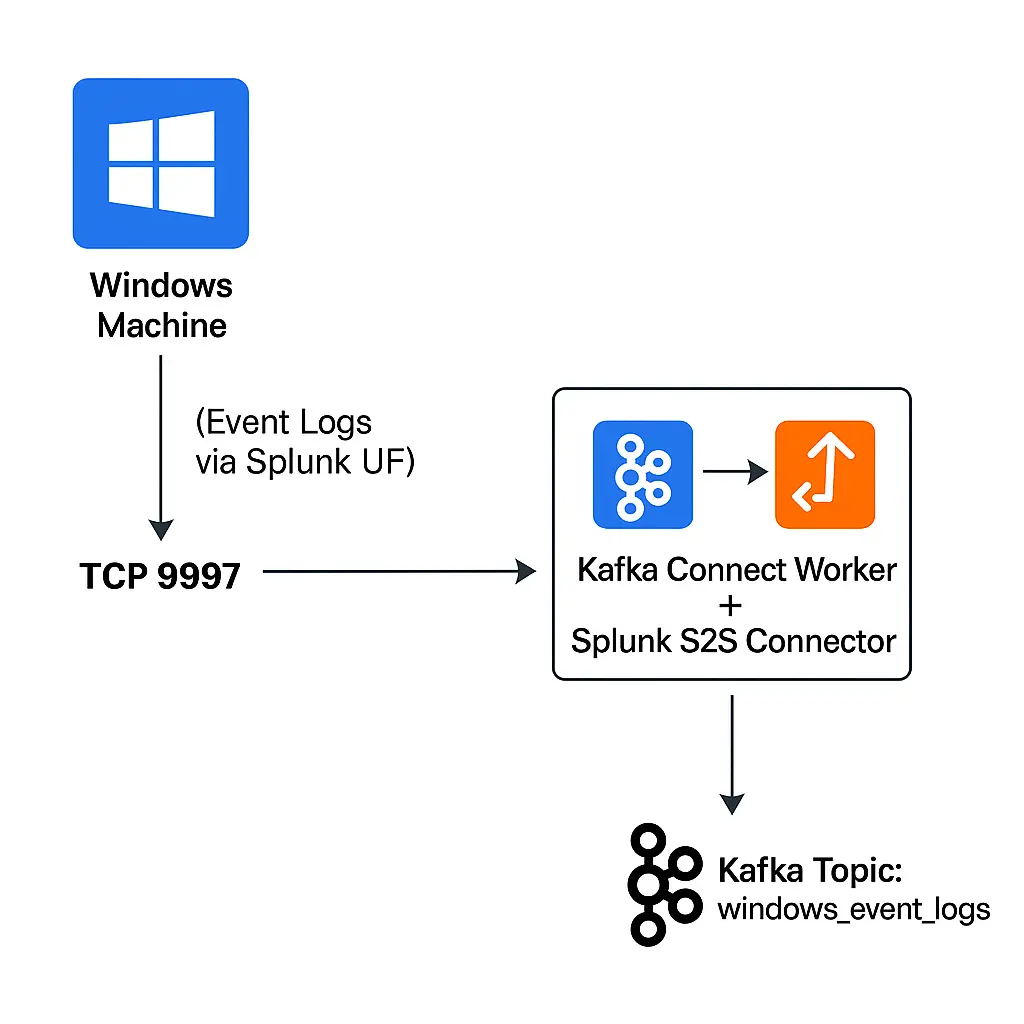
Send Windows Event Logs to Kafka — The Easy Way with Splunk UF & Splunk S2S Kafka Connector
In this blog, I show how to collect Windows Event Logs with Splunk Universal Forwarder and stream them directly into Kafka using the Splunk S2S Connector — no HEC, no scripts, just clean, scalable log shipping.
Automate Your Splunk Queries with splunk_query_runner
The Splunk Query Runner is a lightweight command-line interface (CLI) tool designed to automate the execution of Splunk queries using a straightforward CSV input format. Whether you are executing saved searches, tstats, or dbxquery commands, this tool helps you produce consistent and timestamped outputs with minimal effort. In this blog, we will guide you through its functionality, configuration process, and how it can save you hours in performing repetitive tasks with Splunk.

Splunk Cluster Manager Redundancy - Part 2: Implementation
In this blog, we're going with the manual + DNS-based approach for its simplicity and full control over the switch process. However, since we're running everything on the same physical server (for testing and educational purposes), we're not using distinct hostnames or external DNS. Instead, we'll configure everything using local IPs.
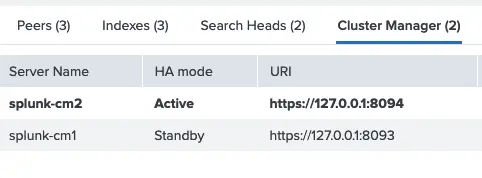
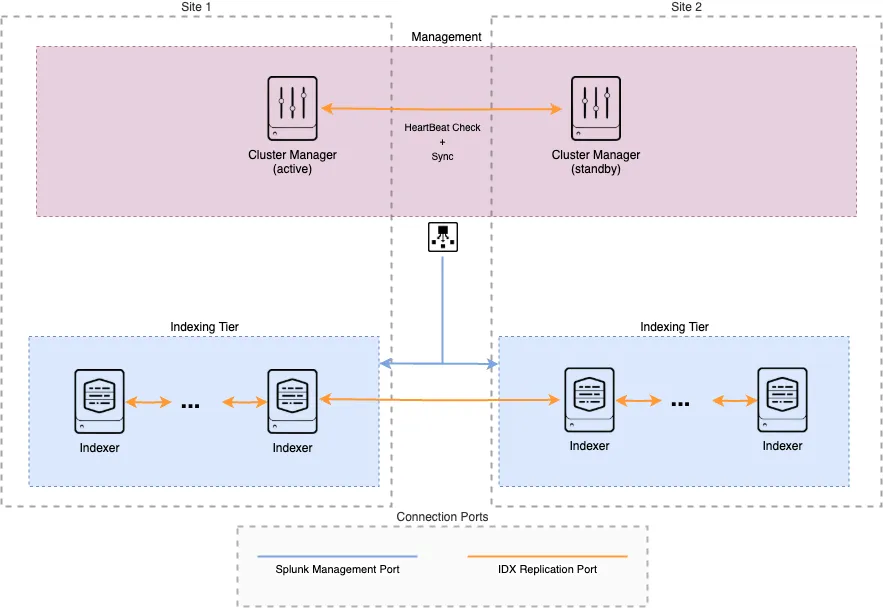
Splunk Cluster Manager Redundancy - Part 1: What it is, why it matters
In distributed Splunk environments, the Cluster Manager (CM) plays a critical role: it coordinates peer nodes, their configuration bundles, and ensures data replication rules are enforced. So… what happens if the Cluster Manager goes down?
Practical Approaches to Tuning ML-Based Correlation Searches in Splunk ES
This study aims to ensure that the correlation rules are effectively implemented using MLTK in practice without any errors.
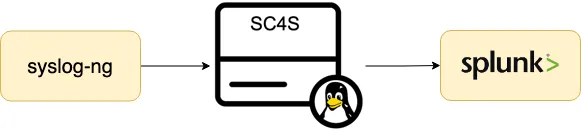
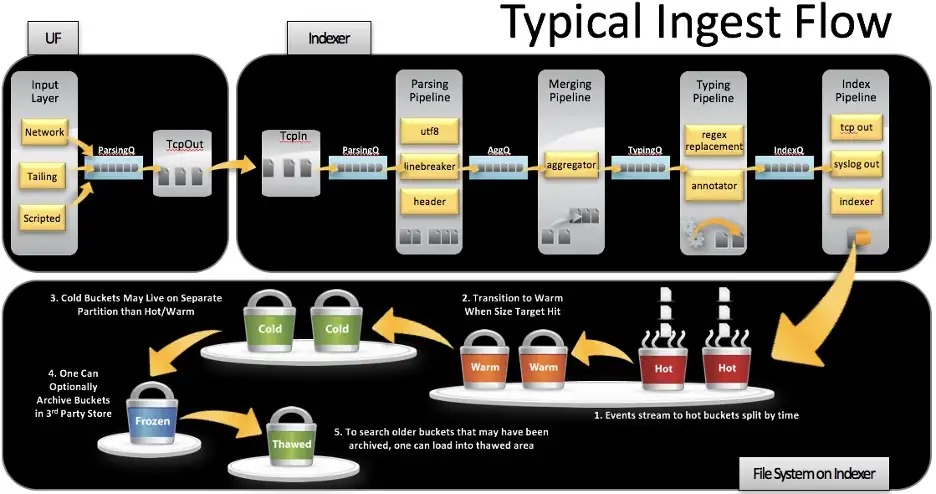
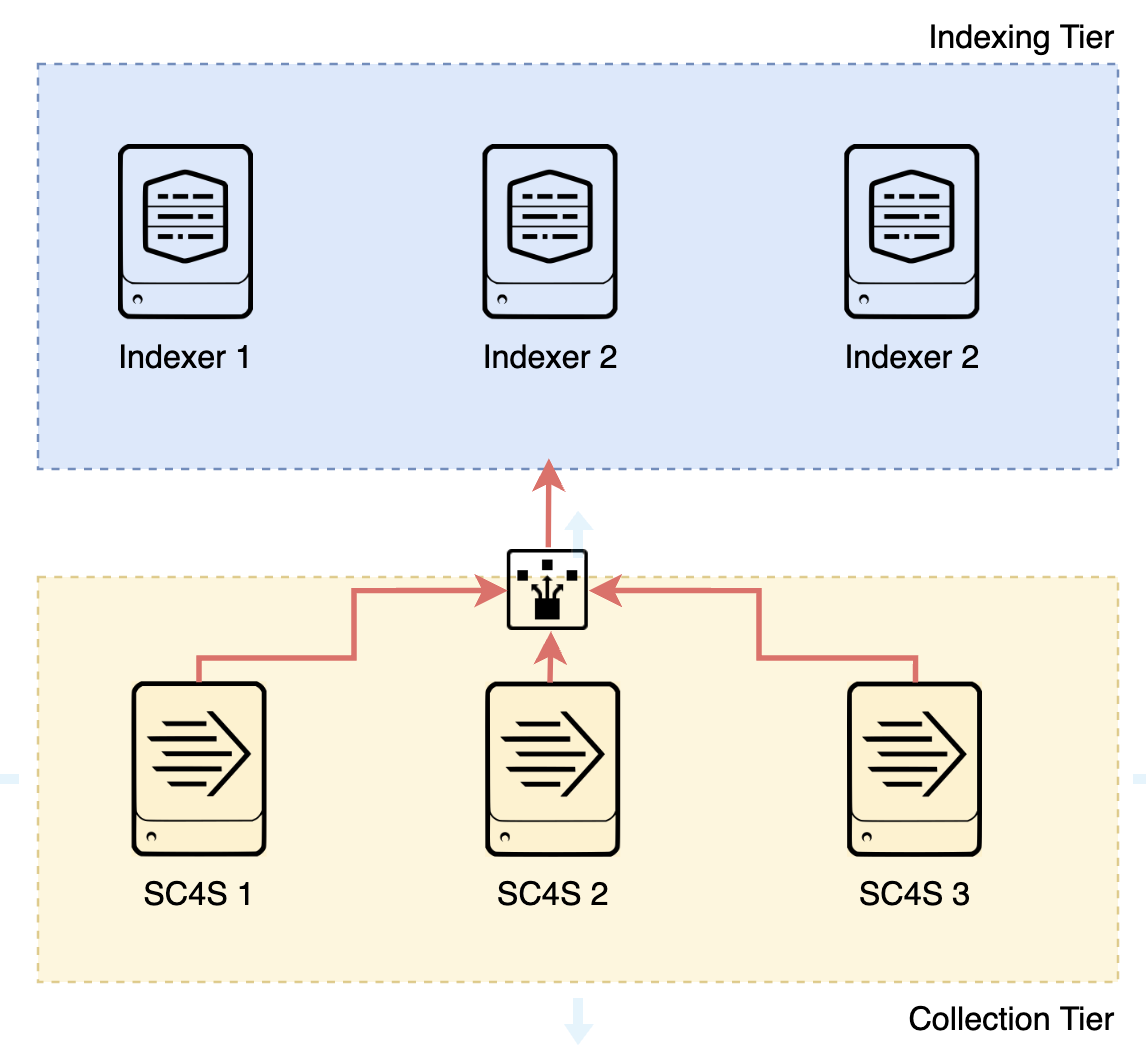
Splunk Connect for Syslog (SC4S): Installation, Usage & Implementations
This blog outlines the installation and the usage of SC4S to import syslog input data into Splunk, addressing various use cases including custom and complex configurations.
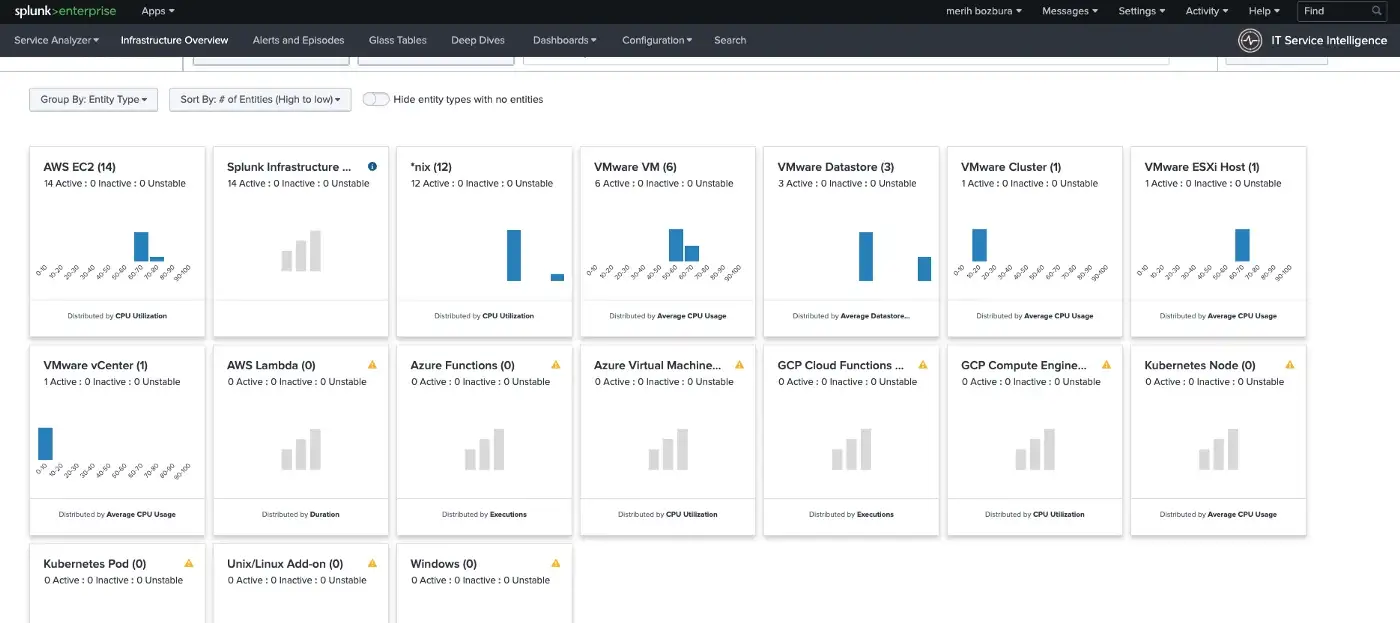
Creating Custom Entity Type with Splunk IT Essentials Work
In this part, you will find out how to create custom entity types and associate entities with IT Essentials Work.
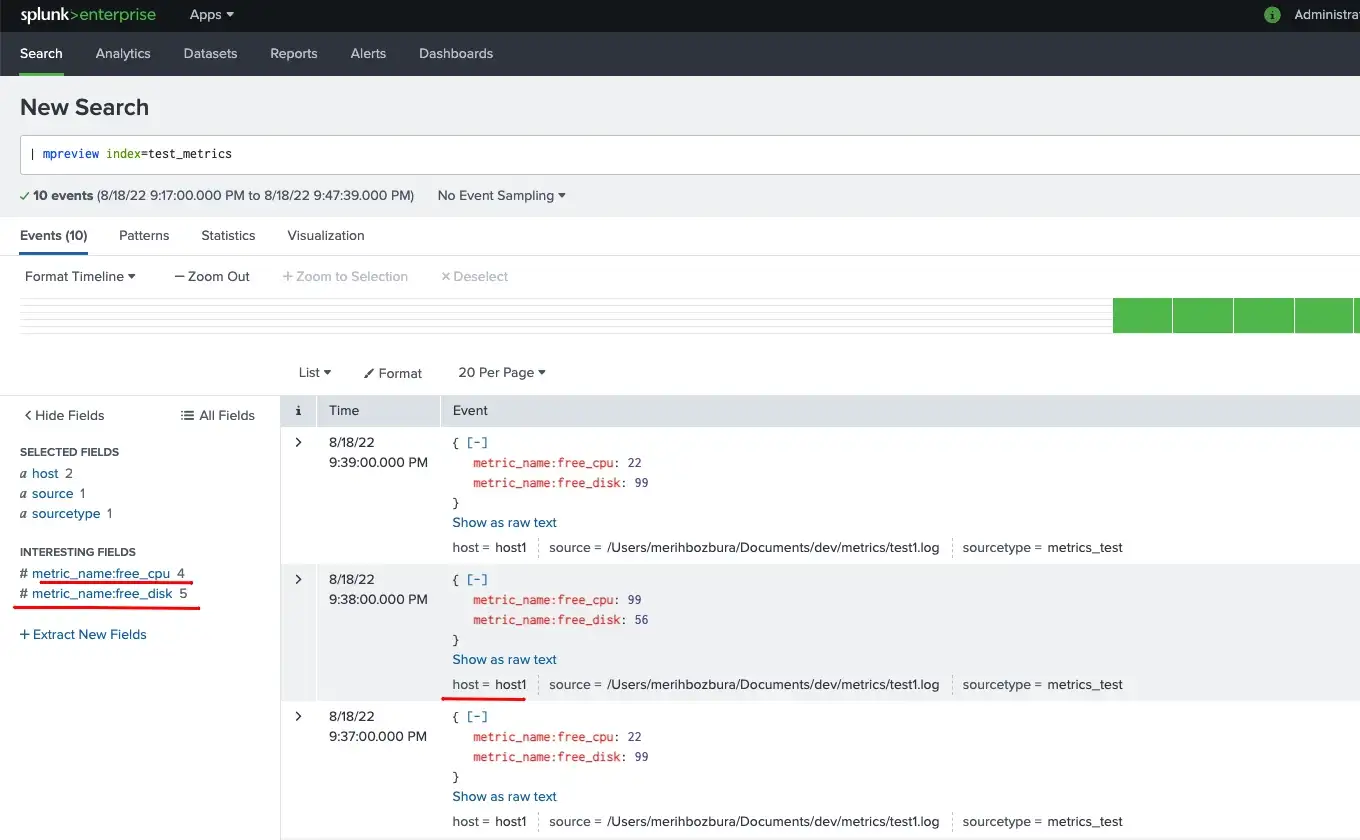
Converting Event Logs into Metrics in Splunk
In this post, you will find out how to convert event logs to metrics and search them in Splunk.
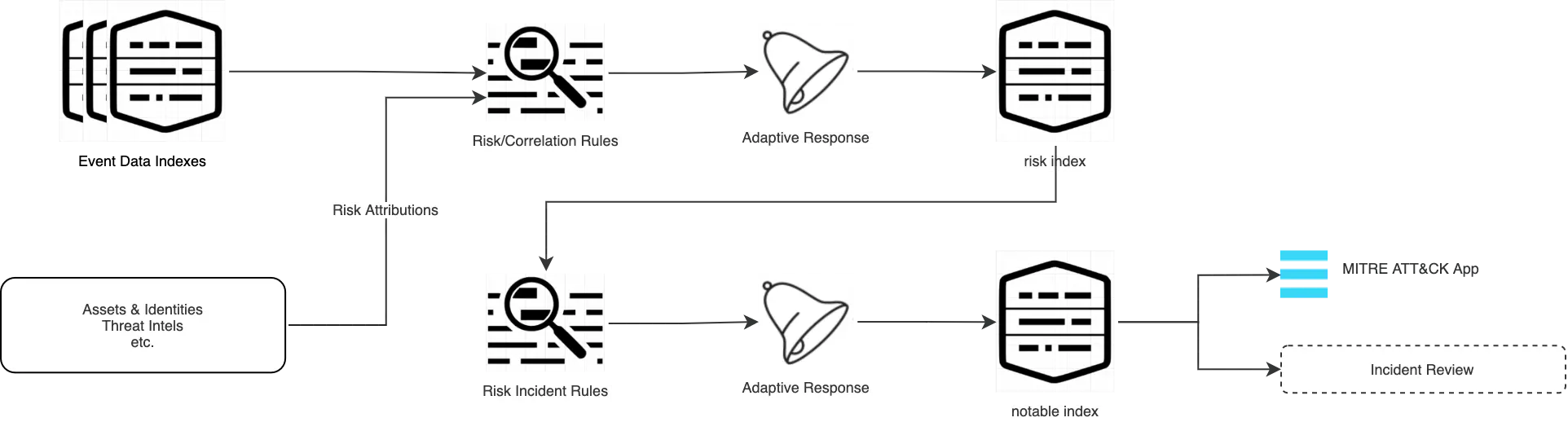
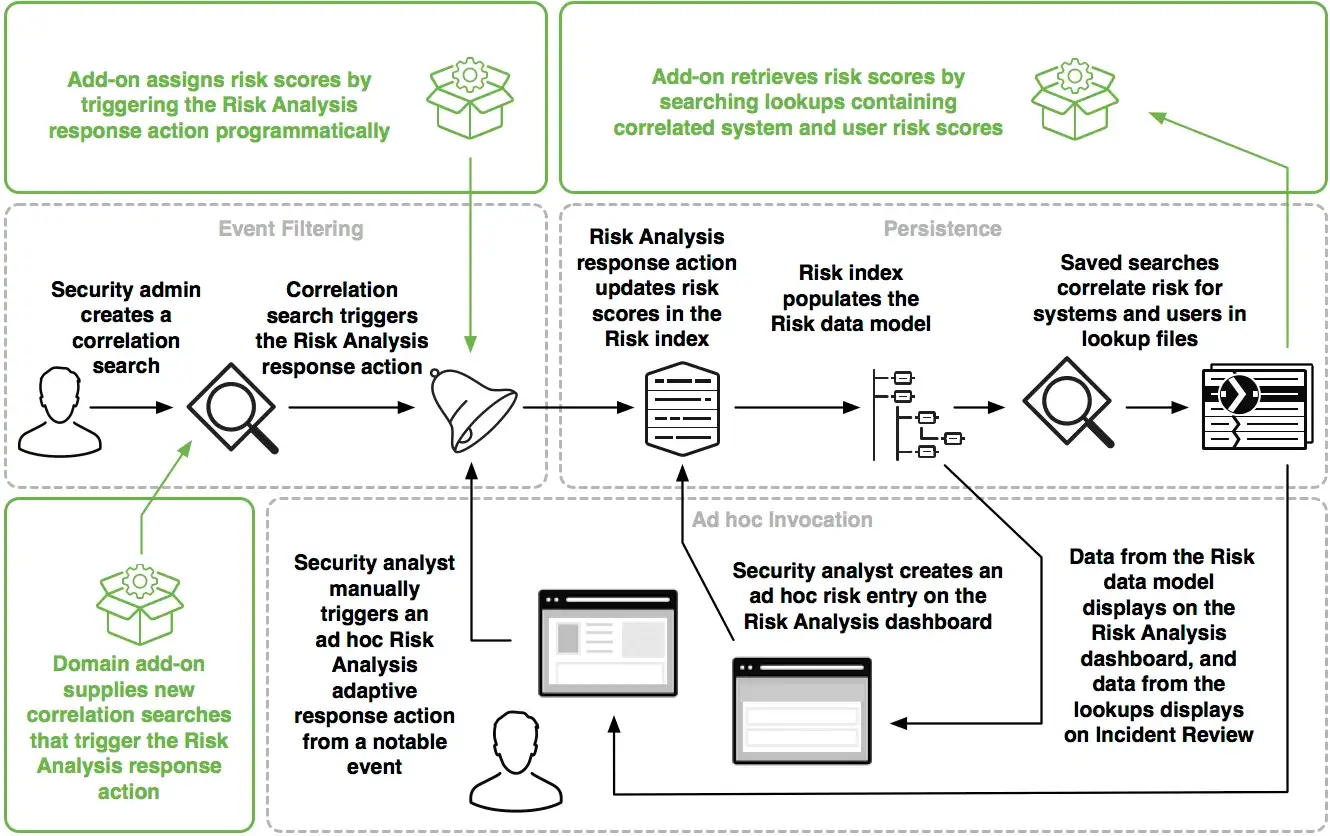
Risk-Based Alerting (RBA) with Splunk Enterprise Security
In this blog, you will find out the abilities of Splunk ES Risk Framework and an idea of how to integrate Risk-Based Alerting into your SOC environment.
Restoring Archived Data with Splunk
In this post, you will find how to utilize https://github.com/seynur/restore-archive-for-splunk to make restoring process smoother.
Syslog Data Collection (SC4S) for Splunk and Custom Inputs
This article provides instructions on how to configure custom syslog inputs (also how to filter out the data) to be ingested to Splunk.
Splunk Data Models & CIM
In this post, you will find out what Splunk data models and CIM (Common Information Model) are and why they hold that much importance.
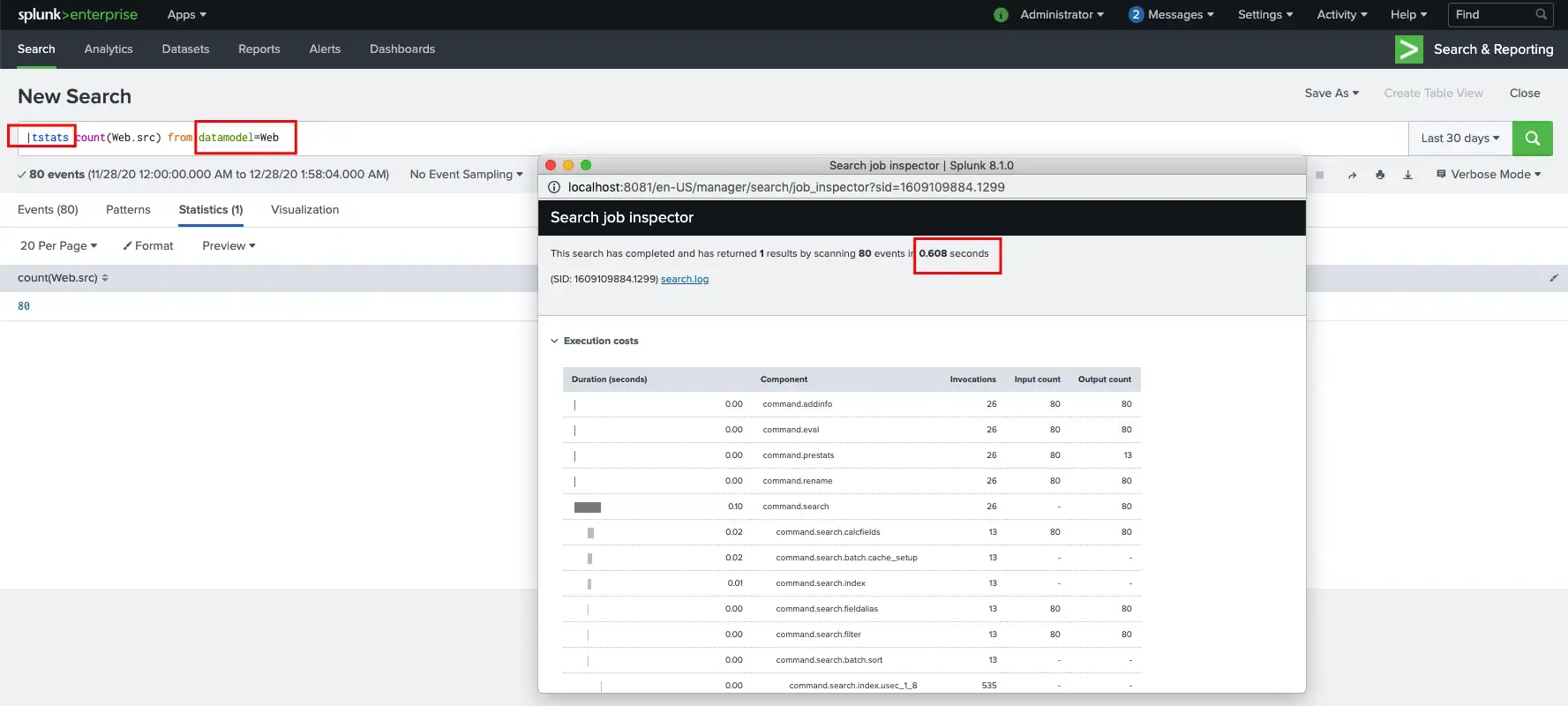
Detecting Cyber Threats with MITRE ATT&CK App for Splunk — Part 3
In this part of the blog series I’d like to focus on writing custom correlation rules. The goal is to utilize MITRE ATT&CK App for Splunk and enrich its abilities ...
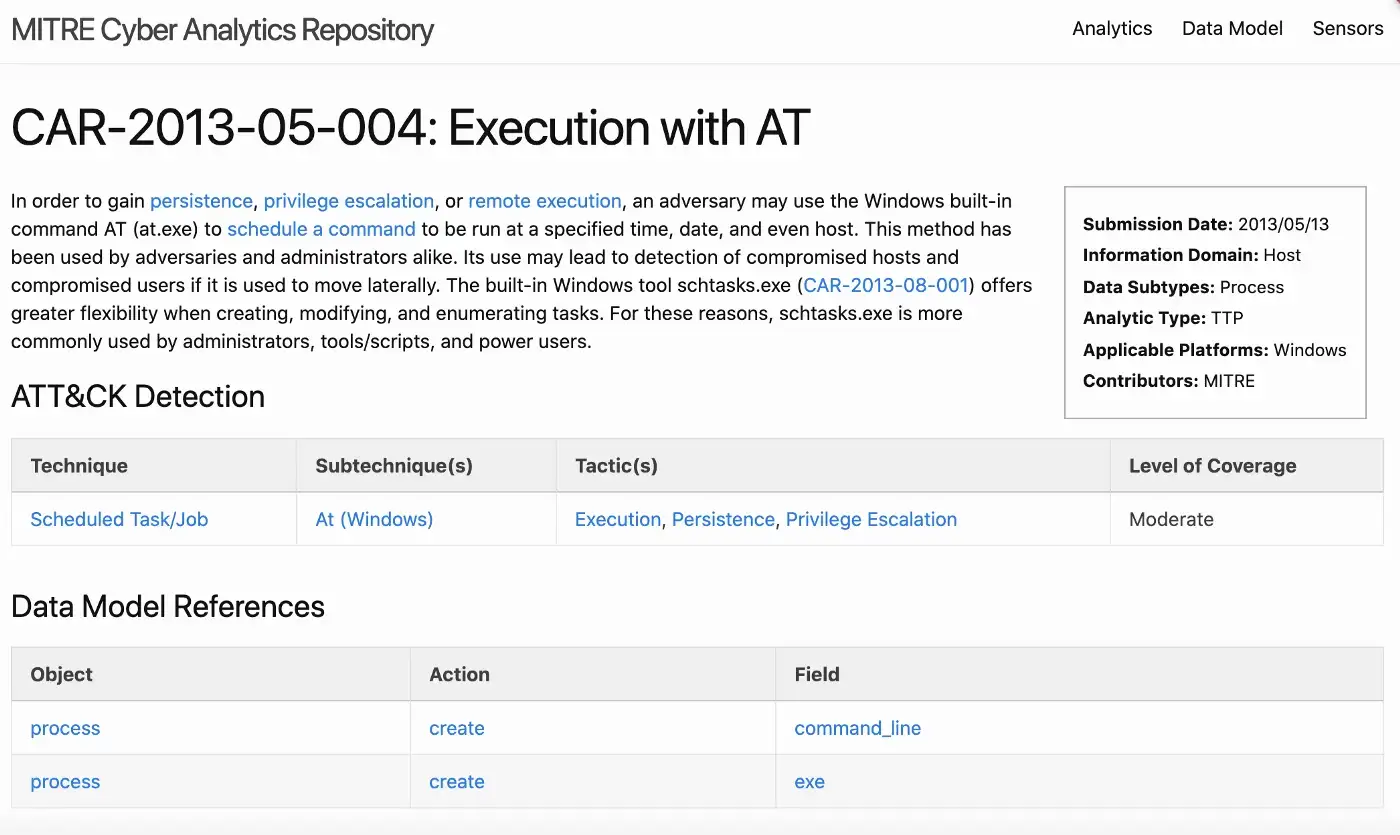
How to Become A Certified Splunk Enterprise Admin?
In this blog, I will talk about the stages of becoming a certified Splunk admin. Splunk is a data (The Data-to-Everything™) platform that allows you to collect any data from any source and analyze it intelligently and generate value from the data.
Detecting Cyber Threats with MITRE ATT&CK App for Splunk — Part 2
In this part of the blog series the goal is to utilize MITRE ATT&CK App for Splunk and associate custom/new correlation ...
Detecting Cyber Threats with MITRE ATT&CK App for Splunk — Part 1
The purpose of this blog post is to share our experience and knowledge in our attempts to detect cyber threats with [Splunk®](https://www.splunk.com). Since we have ...
Kafka
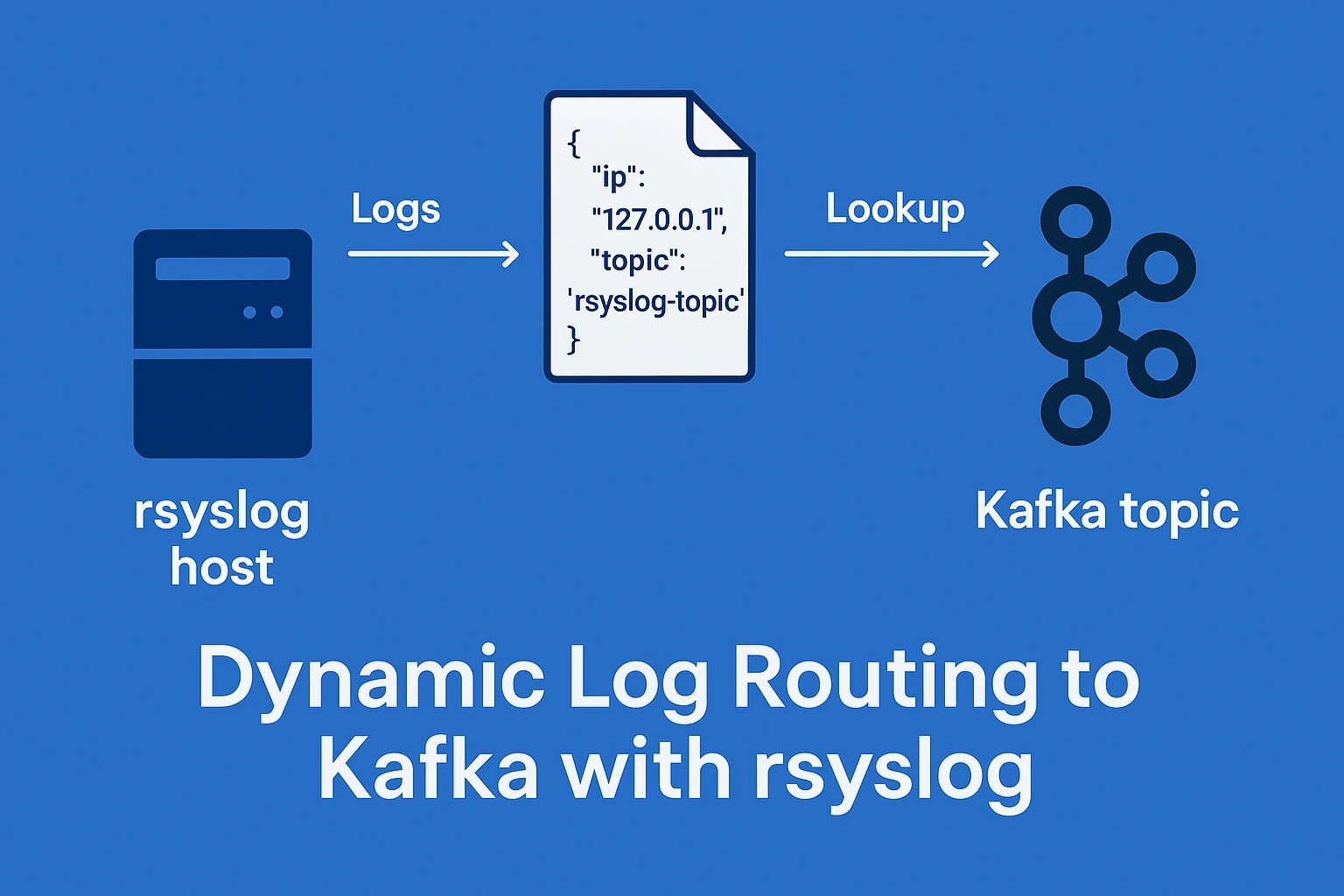
Dynamic Log Routing to Kafka with rsyslog: A Practical Guide You Can Follow
This guide walks through setting up rsyslog to send log data directly to Kafka topics using a dynamic IP-to-topic mapping. We used a simple JSON lookup file to route incoming logs based on their source IP and confirmed delivery using netcat and a Kafka consumer. This lightweight yet powerful approach is ideal for building scalable log pipelines with minimal overhead.
Streaming syslog-ng Events to Kafka: A Practical Guide You Can Follow
This guide walks you through sending logs from syslog-ng to Apache Kafka — step by step, from building components to testing with a sample log. A lightweight, Docker-free setup using Kafka in KRaft mode, perfect for real-time log streaming.
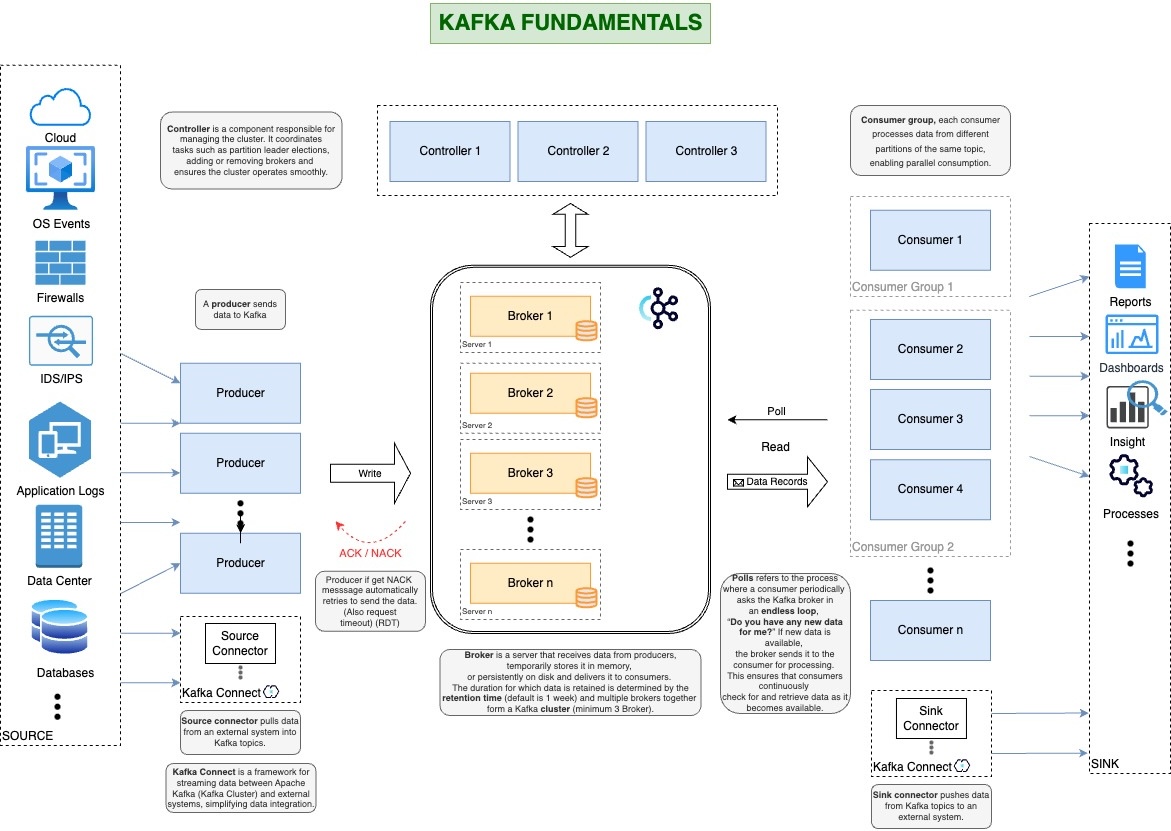
Kafka 101: Core Concepts and How It Works
Apache Kafka is a high-throughput, low-latency, and scalable messaging system. This comprehensive guide covers core concepts, architecture, and hands-on setup using Confluent Platform with KRaft mode.
Ingesting Event Data from Splunk Forwarder/SC4S to Kafka
The goal of this post is to quickly test/analyze methods to send event data from Splunk Forwarders or SC4S to Apache Kafka deployments. There may be several reasons for ...
Ingesting Syslog data to Kafka
When working with event data analytics, especially for security purposes (i.e. SIEM), syslog becomes an important protocol to ingest data. Most of our clients utilize syslog ...
Kafka + S3: Long-term searchable/queryable data retention
The goal of this post is to provide an alternate solution for a question we have started to face with our clients. What is the best way to store event-data in ...

Ansible
Multi-Server Splunk Setup with Ansible & SSH
Automate your Splunk deployment with Ansible: configure SSH access, manage inventories, and roll out installations with ease.

LocalStack
Archiving Splunk Frozen Buckets to S3 on LocalStack
This blog shows how to automatically archive Splunk frozen data to a fully local S3 environment using LocalStack and a custom script, no real cloud required.
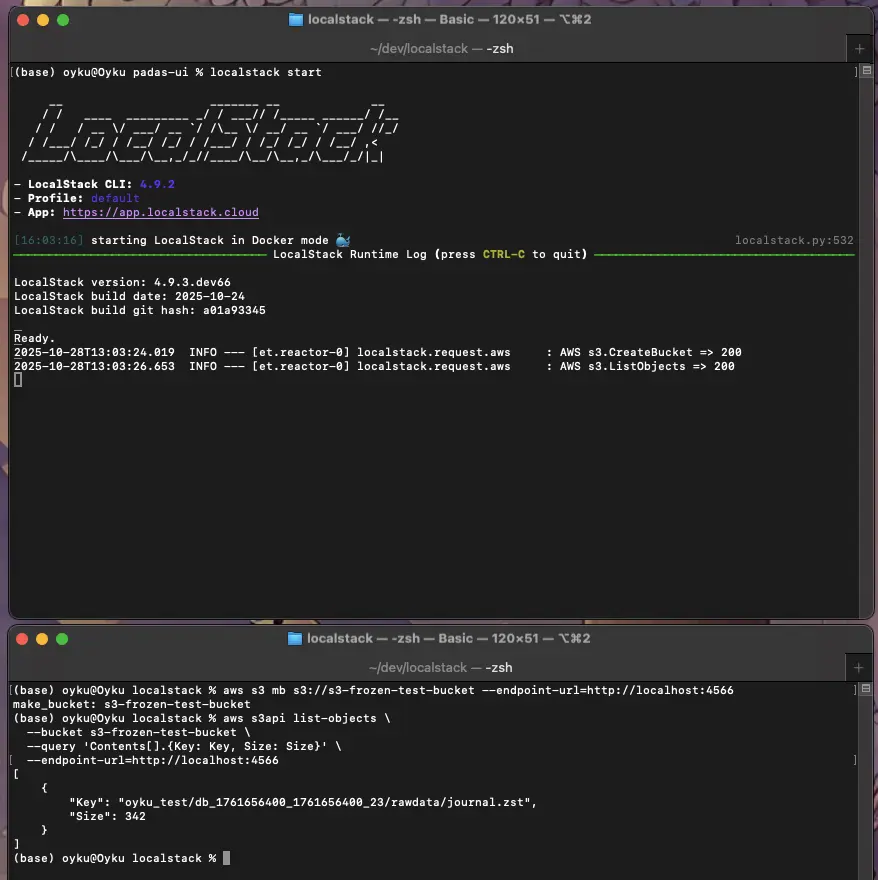
Getting Started with LocalStack: Local S3 Bucket Creation and File Operations
This blog will teach you how to set up a completely local S3 environment using LocalStack and AWS CLI for rapid, cloudless development and testing.

Keepalived
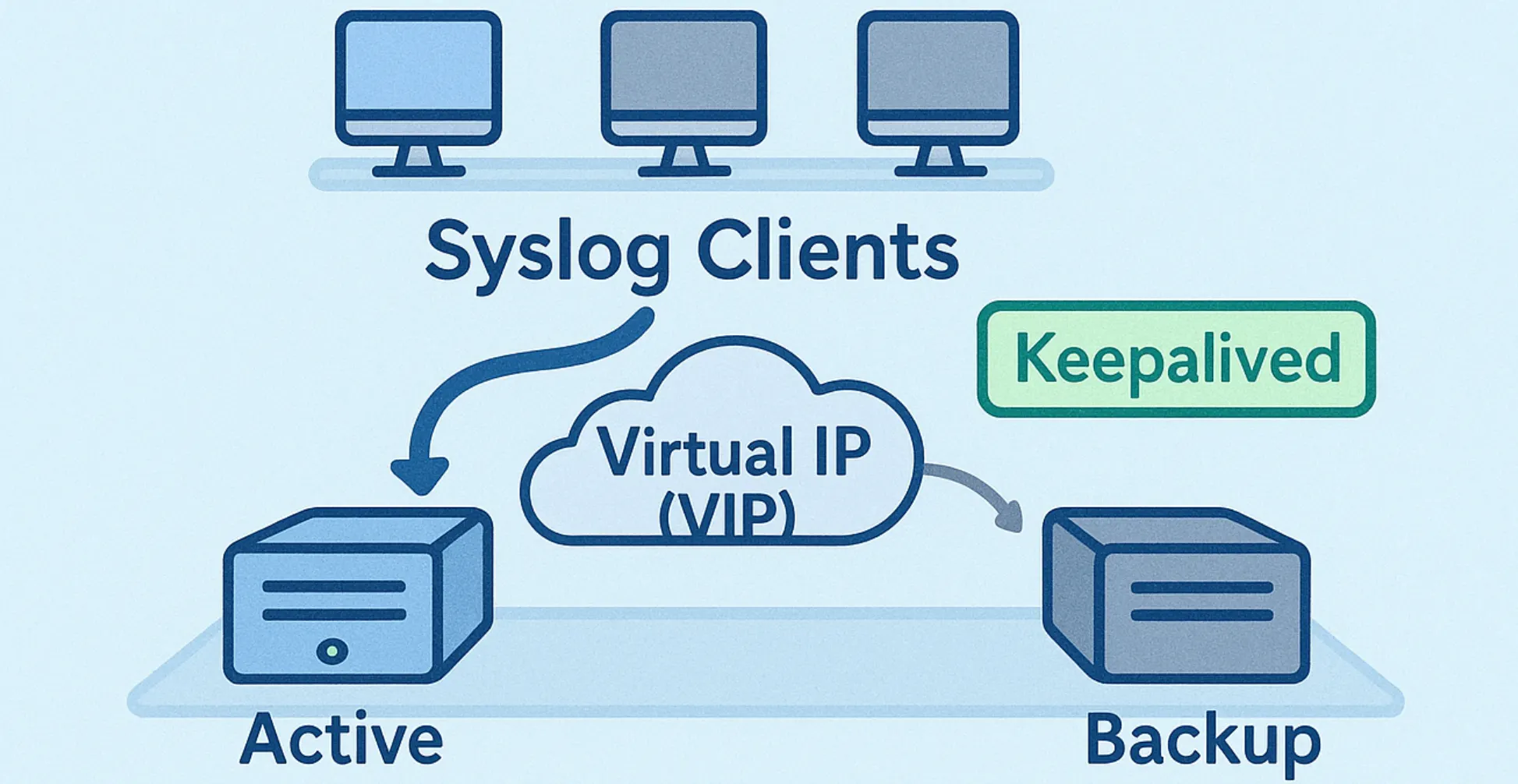
PART 2 — Implementing Keepalived Failover with syslog-ng
This guide shows how to set up a highly available Syslog-ng environment with Keepalived, ensuring continuous log collection and automatic failover via a shared Virtual IP.
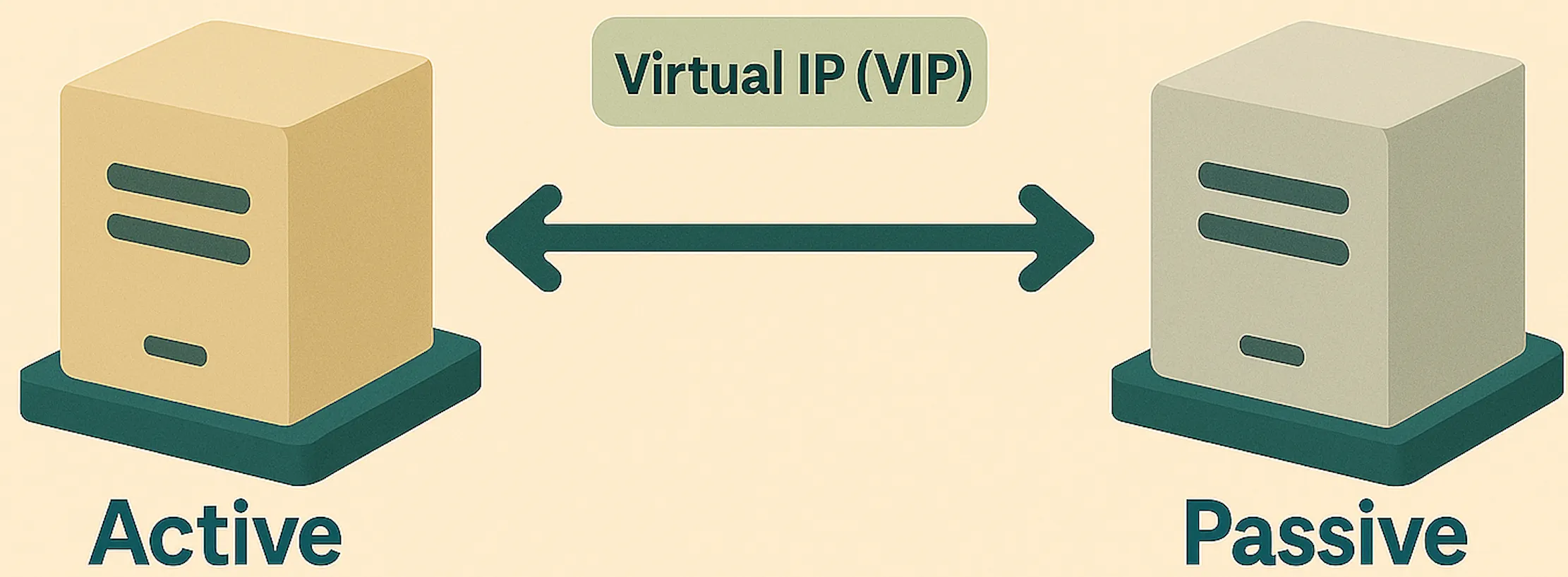
PART 1 — Understanding Keepalived for High Availability
This post explains how Keepalived provides high availability and failover using VRRP (Virtual Router Redundancy Protocol), covering key concepts and configuration basics.